Cybersecurity firm Fortinet’s research indicates more sophistication in malicious actors:
Global cybersecurity firm Fortinet says there is a decline in the organizations detecting ransomware in the first half of 2023, while there is significant activity among Advanced Persistent Threat (APT) groups. In its latest semi-annual Global Threat Landscape Report, prepared by FortiGuard Labs, the cybersecurity firm says there has also been a shift in MITRE ATT&CK techniques used by attackers.
The report says while organizations continue to find themselves in a reactive position due to the growing sophistication of malicious actors and the escalation of targeted attacks, ongoing analysis of the threat landscape have the following highlights:
FEWER DETECTIONS
Organizations detecting ransomware are on the decline: While there is documented substantial spikes in ransomware variant growth in recent years, largely fuelled by the adoption of Ransomware-as-a-Service (RaaS), fewer organizations detected ransomware in the first half of 2023 (13%) compared to this time 5 years ago (22%). Despite the overall decline, organizations must keep their guard up. The trend seen over the last couple of years, is that ransomware and other attacks are becoming increasingly more targeted thanks to the growing sophistication of attackers and the desire to increase the return on investment per attack. Research also found that the volume of ransomware detections continues to be volatile, closing 1H 2023 13x higher than the end of 2022 but still on a downward trend overall when comparing year-over-year.
ATTACK ON EPSS
Malicious actors are 327x more likely to attack top Exploit Prediction Scoring System (EPSS) vulnerabilities within 7 days compared to all other Common Vulnerabilities Exposures (CVEs). 6 years of data spanning more than 11,000 published vulnerabilities that detected exploitation found that the CVEs categorized with a high EPSS score (top 1% severity) are 327x more likely to be exploited within 7 days than any other vulnerability.
HELP FROM RED ZONE
The Red Zone continues to help CISOs prioritize patching efforts: The analysis shows in the second half of 2022, the Red Zone was around 8.9%, meaning that about 1500 CVEs of the more than 16,500 known CVEs were observed under attack. In the first half of 2023, that number dropped slightly to 8.3%. The delta between the 2H 2022 and 1H 2023 is minimal and would seem to be the sweet spot for malicious actors targeting vulnerabilities on endpoints. Still, it is important to note that the number of vulnerabilities discovered, present and exploited constantly fluctuates. These variables and the effectiveness of an organization’s patch management strategy could dramatically decrease its Red Zone surface.
ACTIVE APT GROUPS
Nearly one-third of APT groups were active in 1H 2023: The research shows that that 41 (30%) of the 138 cyberthreat groups MITRE tracks were active in the 1H 2023. Of those, Turla, StrongPity, Winnti, OceanLotus and WildNeutron were the most active based on malware detections. Given the targeted nature and relatively short-lived campaigns of APT and nation-state cyber groups compared to the long life and drawn-out campaigns of cybercriminals, the evolution and volume of activity in this area will be something to look forward to in future reports.
Other highlights of the report:
Unique exploits on the rise: In 1H 2023, there were more than 10,000 unique exploits, up 68% from 5 years ago. The spike in unique exploit detections highlights the sheer volume of malicious attacks security teams must be aware of and how attacks have multiplied and diversified in a relatively short amount of time. There is also a 75% drop in exploitation attempts per organization over a 5-year window and a 10% dip in severe exploits, suggesting that while malicious actor exploit toolkits have grown, the attacks are much more targeted than five years ago.
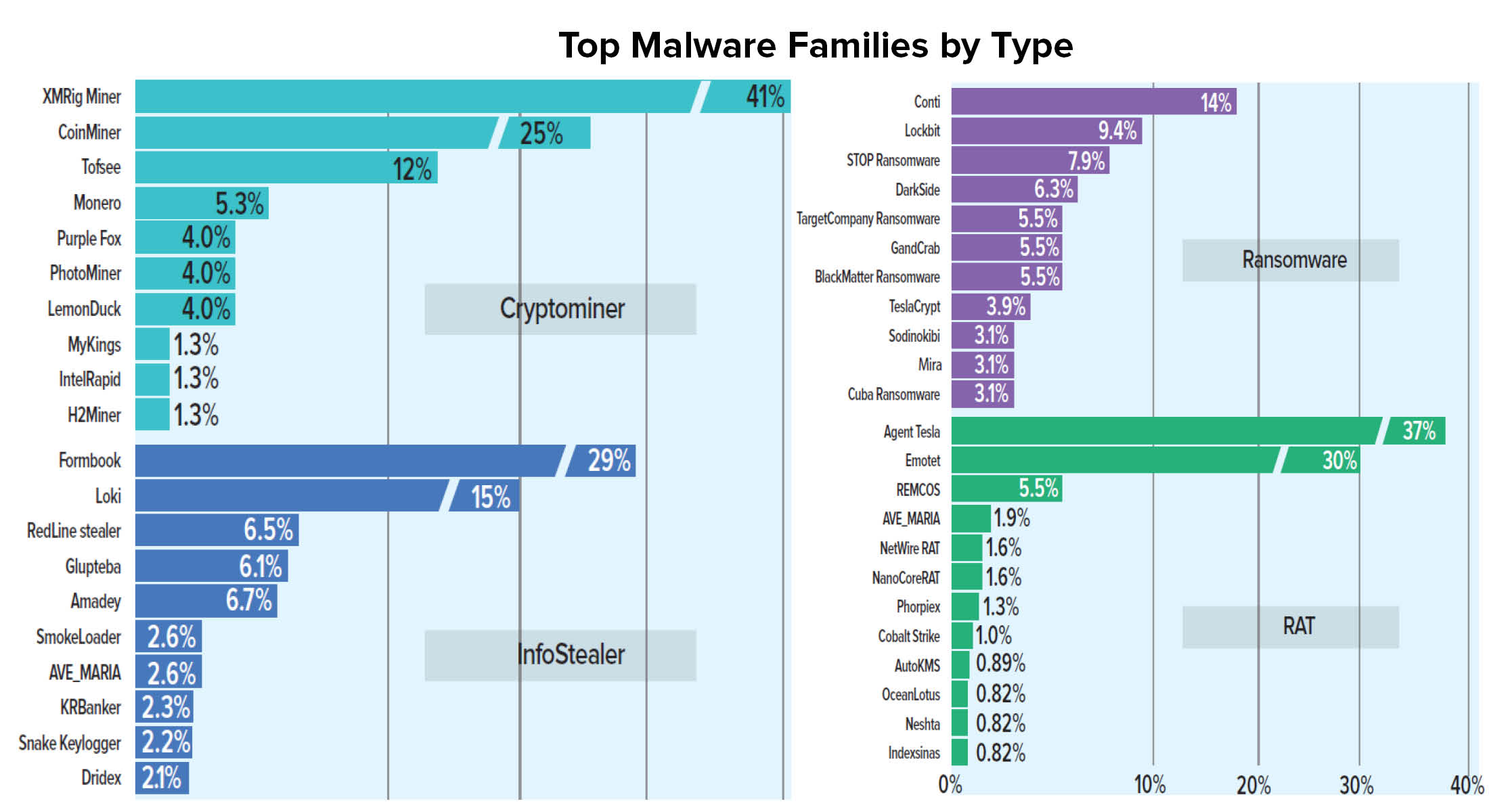
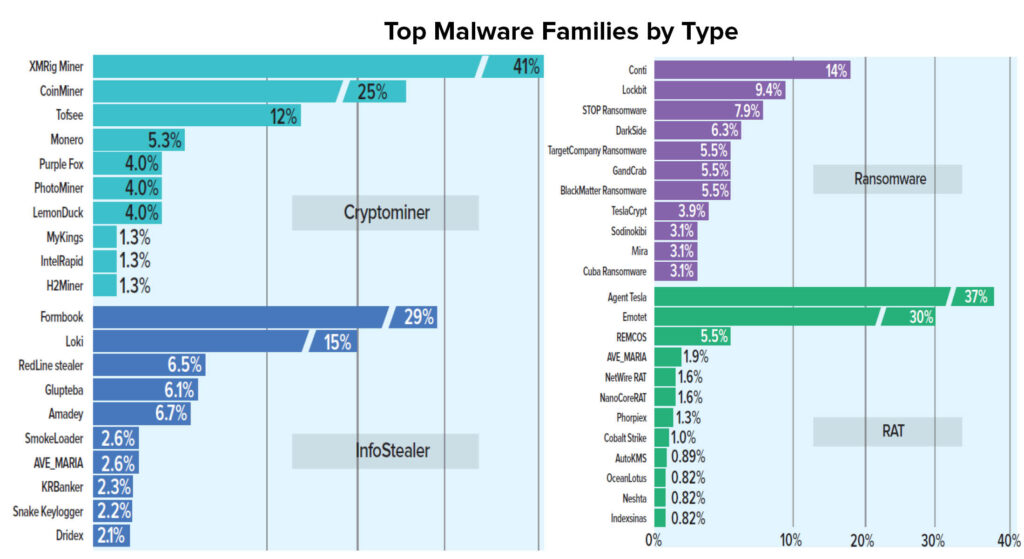
Malware families and variants exploded, up 135% and 175% respectively: In addition to the significant uptick in malware families and variants, another surprising finding is that the number of malware families that propagate to at least 10% of global organizations (a notable prevalence threshold) has doubled over the last five years. This escalation in malware volume and prevalence can be attributed to more cybercriminal and APT groups expanding operations and diversifying their attacks in recent years.
COMMITMENT TO COLLABORATION
FortiGuard Labs says breaking down silos and increasing the quality of actionable threat intelligence help organizations reduce risk and enhances the overall effectiveness of the cybersecurity industry. “Cyber defenders today currently possess access to the tools, knowledge, and support to begin altering the economics of malicious actors. Still, it’s an industrywide commitment to collaboration and intelligence sharing that
will ultimately create a larger ecosystem of disruption and allow the industry to gain the upper hand against cyber adversaries,” it says.
Read more: https://fintechfrontiers.live/google-pays-bnpl-integration-fuels-2024-surge/