
Introduction
Financial Service Institutions (FSI) today rely on layered stacks of SaaS platforms, Virtual Private Networks (VPN), an abundant choice of browsers, a sea of developer tooling sets and AI–assisted analytics. In such environments, a single weakness such as a phishing link, an outdated router, a malicious package, or a browser flaw can rapidly cascade into a major business disruption, data loss and financial impact. Looking back into the recent past, Cybersecurity incidents reported in 2025–2026 send a clear and consistent signal that modern Cybersecurity risk is no longer confined to isolated IT or process failures such as these. Instead, Cybersecurity risk arises from the convergence of identity compromise, legacy infrastructure exposure, software supply–chain abuse and embedded application weaknesses. Undoubtedly, all these operate within deeply inter–connected digital ecosystems.
To remain resilient to these risks, FSI security leaders must move beyond reactive Cybersecurity practices (e.g., patching) and adopt systemic risk management that aligns governance, technology and security architecture and robust forward–looking controls.
Recent Findings
A few recent findings highlight repeatable, well–documented attack vectors with direct business relevance. These findings expose multiple, verifiable attack patterns that share common themes of credential and infrastructure abuse.
- The case of Credential Harvesting & Account Takeover:
A state–sponsored series of coordinated credential–harvesting and espionage operations, the BlueDelta campaign, targeted Microsoft Outlook Web Access, Google, and Sophos VPN users through multi–stage phishing that displays legitimate PDFs before redirecting victims to spoofed login pages, harvesting credentials invisibly before redirecting to the real site to avoid suspicion.
The operation relied on disposable hosting tools to host fake portals and collect stolen logins at scale. The hosting tools included webhook.site (a web service that gives an instant, unique URL), InfinityFree (a free web–hosting provider that allows users to host websites with unlimited disk space and bandwidth at zero cost), and ngrok (a tunneling service that exposes a local service (e.g., an app on localhost) to the internet via a secure public URL).
Impact:
Nation–state actors like BlueDelta steal OWA, Google, and VPN credentials and silently access mailboxes and networks, enabling long–term espionage and lateral movement. This exposes the victim Institutions to risks and consequences across strategic communications, negotiations and sensitive IP with direct regulatory and reputational impacts.
- The case of Local privilege abuse and endpoint control weaknesses
This is a classic example of unauthorized access, wherein research has shown that unprivileged users can gain unauthorized control of system administration profiles and daemon logging (i.e., logging done by or for background system services, usually on Unix or Linux based systems. Simply put, a daemon is a background service that runs without direct user interaction). This action creates potential for denial–of–service and stealthy tampering on multi–user or shared systems.
Impacting Linux laptops, desktops and workstations where Linux power management utility (TLP) version 1.9.0 is installed, a critical flaw in the TLP allows local attackers to bypass Polkit authentication (i.e., the authorization mechanism Linux services use to decide whether a user or process is allowed to perform a privileged action) and manipulate power settings. In Cybersecurity circles, this exposure is tracked as “CVE–2025–67859”.
Impact:
Local auth–bypass flaws such as TLP and Polkit allow unauthorized users or malware gain control over system behavior and logging. This weakens endpoint security, impairs detection and forensics, and increases the risk and cost of broader compromises on shared or high–value systems. This can in turn lead to other impacts to Institutions across financial, reputational, regulatory, privacy and other dimensions.
- The case of Browser and embedded WebView exposure
In the popular Google’s Chrome browser, a high–severity WebView vulnerability stemming from insufficient policy enforcement lets attackers bypass security restrictions in apps embedding web content and enable data leakage and code execution inside trusted applications.
A WebView is a web browser that is embedded within an app. It acts like a mini–browser inside the app to show web pages, interactive guides or entire web–based app sections. WebView is widely used inside desktop and mobile applications, and their exploitation risks include unauthorized access, data leakage and malicious code execution within normally trusted app contexts. Google has released an emergency fix for this issue, and this is tracked as “CVE–2026–0628”.
Impact:
High–risk WebView bugs in Chrome allow malicious extensions or pages to bypass policy enforcement and inject code into privileged web apps and in–app flows. That can lead to theft of Software–as–a–Service (SaaS) credentials, session tokens and transaction data. These revoke users trust in customer–facing portals and internal web systems.
- The case of Software supply–chain and developer–targeted malware
And yet, another instance of technology infrastructure abuse came to light in 2025 and continues into 2026. In a recent Cybersecurity incident involving NodeCordRAT, three malicious npm packages (“bitcoin–main–lib”, “bitcoin–lib–js”, and “bip40”) were uploaded to the npm package registry to impersonate “bitcoinjs”–related libraries and silently install NodeCordRAT on developer machines.
NodeCordRAT is a new family of malicious Remote Access Trojans (RATs) that targets developers by masquerading as legitimate libraries within the “npm” package registry. “npm” or Node Package Manager is the world’s largest Software Library / Registry containing over 800,000 code packages. Developers around that world use npm packages as reusable bundles of JavaScript code (modules) that are published to the npm package registry.
This incident led to exfiltrating credentials, secrets and crypto wallets via Discord–based Command and control (C2). For context, Discord is a chat, voice, and video service enabling users to join and create communities associated with their interests, while C2 is a malicious technique where Cybersecurity attackers use the legitimate Discord platform’s infrastructure and Application Programming Interface (APIs) to remotely control compromised systems and exfiltrate data.
In this incident, NodeCordRAT used Discord as C2, exfiltrating browser logins, environment variables in “.env” files and MetaMask wallet data, giving attackers live remote control and direct access to sensitive project and credential stores. MetaMask is a popular self–custodial crypto wallet and gateway to Web3. Available as a browser extension and mobile app, it allows users manage digital assets like ETH & tokens and interact with decentralized applications (“dapps”) on the Ethereum blockchain and other Ethereum Virtual Machine (EVM) compatible networks. These networks are blockchains by themselves that can run smart contracts designed for the EVM.
Impact:
Malicious “npm” packages that drop RATs (like NodeCordRAT) turn developer machines into high–value breach points, exfiltrating source code, secrets, and wallet data. This opens the door to poisoned builds, backdoor software releases, IP theft and significant brand and liability exposure for software–producing Institutions.
- The case of Legacy infrastructure and Large–scale business disruption
We all know that legacy infrastructure is not just a technical debt issue, but it directly translates into exploitable edge devices and fragile production environments that can drive major revenue and supply–chain shocks. Cases involving two reputed companies are apt representatives of this well–recognized business problem.
- D–Link
The D–Link case is a textbook example of how long–forgotten, End–of–Life (EoL) devices become high–leverage and exploitable entry points. Continuing to run unsupported network hardware creates an unbound risk that anyone on the internet or on the Local Area Network (LAN) can exploit and seize critical connectivity devices that have no vendor–supplied remediation measures.
A new command–injection flaw in legacy D–Link DSL routers exploited via the “dnscfg.cgi” endpoint, enables unauthenticated remote code execution on EoL devices that are no longer supported or patched. Multiple D–Link DSL gateway routers (DSL–526B, DSL–2640B, DSL–2740R, DSL–2780B) went EoL in 2020. The “dnscfg.cgi” endpoint in these routers was exploited by a command–injection vulnerability, “CVE–2026–0625”.
Impact:
For various businesses or Internet Service Providers (ISP) that continue to rely on these EoL units, exploitation of this vulnerability can disrupt customer connectivity, enable credential interception, or provide staging for larger intrusions against back–office systems and have the potential to convert into significant business losses. D–Link does not provide firmware patches to these devices as these are EoL and D–Link recommends retiring or replacing these models.
- Jaguar Land Rover
The Jaguar Land Rover (JLR) case shows the downstream effect when critical environments are not sufficiently segmented or made resilient against cyberattacks. This incident led to a 43% drop in wholesale volumes in Q3 2025 for JLR through significant production outages and financial stress on suppliers. It is also a stark reflection of legacy and architectural weaknesses in technology systems, resulting from the combined usage of valid accounts, exposed applications, broad lateral movement of attackers resulting into a need to shut down inter-connected systems.
Reports indicate that attackers exploited JLR’s public–facing applications and then used valid accounts and remote services to move laterally through core enterprise systems. Industry analysis reveals weak segmentation and credential abuse as the key exploit of how the attackers moved through JLR’s network and escalated privileges across one or more key applications. Once the attackers gained initial access, there were insufficient internal boundaries between internet–facing apps, internal domains, production, and logistics systems to prevent their advances. The legacy architecture and out–of–date elements of these systems forced JLR to shut down large parts of the production process, blocked dealer registrations, and disrupted parts supply for several weeks. Normal operations restored by November 2025.
Impact:
The disruption caused cash–flow strain for JLR’s suppliers and dealers. This was so significant that the UK government intervened and provided a £1.5 billion loan guarantee to support JLR and stabilize its supply chain. JLR recorded £196 million in direct costs in Q3 2025 due to the attack and the Bank of England cited this incident as one of the factors that weakened the UK GDP in Q3 2025.
This incident illustrates how a single Cybersecurity incident can propagate through manufacturing and supply chains, all at once and cause serious damage to several businesses and the economy.
Addressing Inter–connected Cybersecurity Risk
Collectively, the incidents described above demonstrate that identity, legacy edge devices, developer tooling and embedded web components are now prime attack surfaces with direct business impact.
Addressing the inter-connected risks such as the ones highlighted here requires Institutions to shift from reactive engagements to proactive systemic risk management anchored in proven practices of identity management, solution and security architecture, and software supply chain discipline. Given below are a few tasks that Institutions should consider to strengthen their Cybersecurity defences.
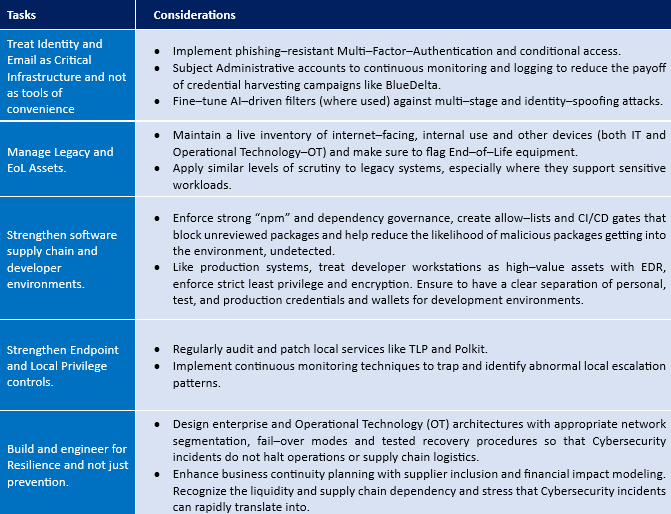
Supporting Cybersecurity and AI Framework Controls
Both the NIST Cybersecurity Framework 2.0 (CSF) and the NIST AI Risk Management Framework (AI RMF) are excellent resources to address these types of inter–connected risks. Given below are a selection of controls from these two frameworks for this purpose.
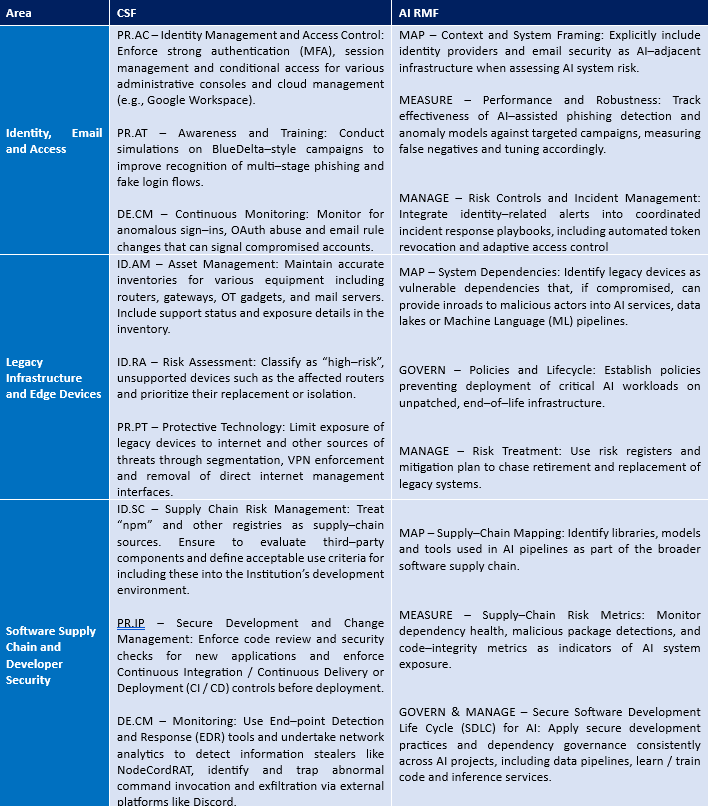
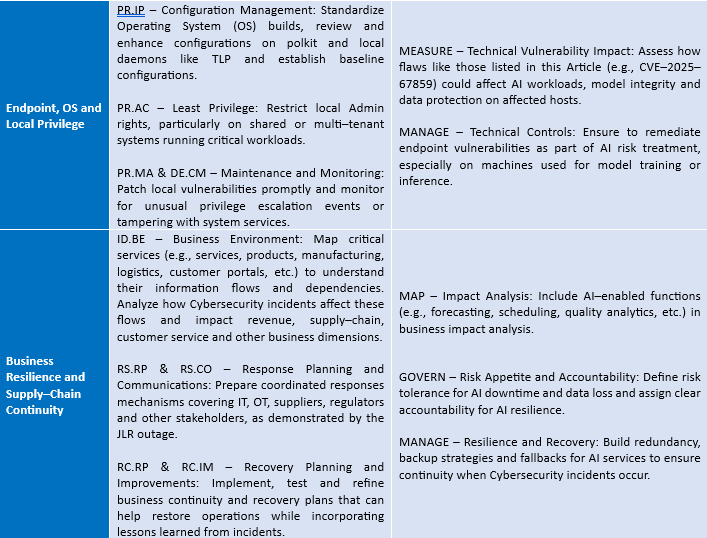
Closing Thoughts
The incidents discussed in this Article are not isolated anomalies. They are early warnings about structural weaknesses in how identity, infrastructure and software supply chains are mis-aligned. Clearly, a series of failures among people, process, and technology are evident. Organizations that respond through diligent, disciplined and effective programs with strong controls in specific areas of Identity and Access Management, Legacy Technology Management, Developer Tooling and Practices, and Business Resilience and Incident Management will be better positioned to withstand the next wave of attacks and to preserve trust in both their digital and AI–enabled operations. Industry frameworks such as the NIST CSF and NIST AI RMF included in this Article are guardrails to enable and direct Institutions to meet these control objectives.
Ultimately, Cybersecurity resilience is no longer a technical aspiration. It is a business survival requirement.
- What is your view on inter-connected Cybersecurity risks?
- Is your Cybersecurity program aligned to AI–era risk, or is it still designed for yesterday’s threats?
- How confident are you that a minor Cybersecurity event will not cascade into a major regulatory or operational crisis?
About This Article:
This Article explores how inter-connected Cybersecurity risks arising from credential theft, endpoint weaknesses, browser and WebView flaws, software supply–chain compromise, legacy edge devices and large–scale operational outages are converging into enterprise–level business threats that equally apply to financial institutions and other regulated industries. Drawing on a few recent cases in the real world, this Article shows that technical gaps in identity, infrastructure and architecture directly manifest as revenue loss, supply–chain disruption, regulatory exposure, and erosion of stakeholder trust.
Authored by Narasimham Nittala and published as part of Financial Technology Frontiers (FTF)’s Hi2AI Series, this Article demonstrates how seemingly isolated technical vulnerabilities can cascade into operational disruption, regulatory exposure and loss of trust, by grounding the analysis in recent, real–world incidents. It further shows how aligning an institution’s Cybersecurity programs with NIST CSF and extending governance through the NIST AI RMF can help institutions move from reactive defense to proactive, resilient risk management in the AI era. Like our previously published Articles, this is also written in an accessible, practitioner–focused format and it aims to raise awareness about responsible AI adoption across Financial Institutions.
FTF believes that financial service providers, Fintech entities, consulting firms, and technology companies can all benefit from reflecting on the perspectives shared here and consider how their own approaches to AI Risk Management can evolve. Practitioners in other industries are equally encouraged to adapt these insights to their unique contexts.
About Hi2AI
Hi2AI is FTF’s AI ecosystem For Financial Services. Hi2AI is a trusted community shaping the future of Artificial Intelligence in Financial Services by driving responsible innovation, influencing policy with regulators, and crafting future standards that ensure growth, resilience, and trust across the global financial ecosystem. Hi2AI exists to accelerate the responsible adoption of AI across the global financial ecosystem through:
- AI–Driven Industry Collaboration.
- Ecosystem Connection & Innovation.
About Financial Technology Frontiers
Financial Technology Frontiers (FTF) is a global media–led fintech platform dedicated to building and nurturing innovation ecosystems. We bring together thought leaders, financial institutions, fintech disruptors, and technology pioneers to drive meaningful change in the financial services industry.
All sources are hyperlinked.




